- Blog Categories
- Project Management
- Agile Management
- IT Service Management
- Cloud Computing
- Business Management
- Business Intelligence
- Quality Engineer
- Cyber Security
- Career
- Big Data
- Programming
- Most Popular Blogs
- PMP Exam Schedule for 2024: Check PMP Exam Date
- Top 60+ PMP Exam Questions and Answers for 2024
- PMP Cheat Sheet and PMP Formulas To Use in 2024
- What is PMP Process? A Complete List of 49 Processes of PMP
- Top 15+ Project Management Case Studies with Examples 2024
- Top Picks by Authors
- Top 170 Project Management Research Topics
- What is Effective Communication: Definition
- How to Create a Project Plan in Excel in 2024?
- PMP Certification Exam Eligibility in 2024 [A Complete Checklist]
- PMP Certification Fees - All Aspects of PMP Certification Fee
- Most Popular Blogs
- CSM vs PSM: Which Certification to Choose in 2024?
- How Much Does Scrum Master Certification Cost in 2024?
- CSPO vs PSPO Certification: What to Choose in 2024?
- 8 Best Scrum Master Certifications to Pursue in 2024
- Safe Agilist Exam: A Complete Study Guide 2024
- Top Picks by Authors
- SAFe vs Agile: Difference Between Scaled Agile and Agile
- Top 21 Scrum Best Practices for Efficient Agile Workflow
- 30 User Story Examples and Templates to Use in 2024
- State of Agile: Things You Need to Know
- Top 24 Career Benefits of a Certifed Scrum Master
- Most Popular Blogs
- ITIL Certification Cost in 2024 [Exam Fee & Other Expenses]
- Top 17 Required Skills for System Administrator in 2024
- How Effective Is Itil Certification for a Job Switch?
- IT Service Management (ITSM) Role and Responsibilities
- Top 25 Service Based Companies in India in 2024
- Top Picks by Authors
- What is Escalation Matrix & How Does It Work? [Types, Process]
- ITIL Service Operation: Phases, Functions, Best Practices
- 10 Best Facility Management Software in 2024
- What is Service Request Management in ITIL? Example, Steps, Tips
- An Introduction To ITIL® Exam
- Most Popular Blogs
- A Complete AWS Cheat Sheet: Important Topics Covered
- Top AWS Solution Architect Projects in 2024
- 15 Best Azure Certifications 2024: Which one to Choose?
- Top 22 Cloud Computing Project Ideas in 2024 [Source Code]
- How to Become an Azure Data Engineer? 2024 Roadmap
- Top Picks by Authors
- Top 40 IoT Project Ideas and Topics in 2024 [Source Code]
- The Future of AWS: Top Trends & Predictions in 2024
- AWS Solutions Architect vs AWS Developer [Key Differences]
- Top 20 Azure Data Engineering Projects in 2024 [Source Code]
- 25 Best Cloud Computing Tools in 2024
- Most Popular Blogs
- Company Analysis Report: Examples, Templates, Components
- 400 Trending Business Management Research Topics
- Business Analysis Body of Knowledge (BABOK): Guide
- ECBA Certification: Is it Worth it?
- How to Become Business Analyst in 2024? Step-by-Step
- Top Picks by Authors
- Top 20 Business Analytics Project in 2024 [With Source Code]
- ECBA Certification Cost Across Countries
- Top 9 Free Business Requirements Document (BRD) Templates
- Business Analyst Job Description in 2024 [Key Responsibility]
- Business Analysis Framework: Elements, Process, Techniques
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Career Options after BCom to Know in 2024
- Top 10 Power Bi Books of 2024 [Beginners to Experienced]
- Power BI Skills in Demand: How to Stand Out in the Job Market
- Top 15 Power BI Project Ideas
- Top Picks by Authors
- 10 Limitations of Power BI: You Must Know in 2024
- Top 45 Career Options After BBA in 2024 [With Salary]
- Top Power BI Dashboard Templates of 2024
- What is Power BI Used For - Practical Applications Of Power BI
- SSRS Vs Power BI - What are the Key Differences?
- Most Popular Blogs
- Data Collection Plan For Six Sigma: How to Create One?
- Quality Engineer Resume for 2024 [Examples + Tips]
- 20 Best Quality Management Certifications That Pay Well in 2024
- Six Sigma in Operations Management [A Brief Introduction]
- Top Picks by Authors
- Six Sigma Green Belt vs PMP: What's the Difference
- Quality Management: Definition, Importance, Components
- Adding Green Belt Certifications to Your Resume
- Six Sigma Green Belt in Healthcare: Concepts, Benefits and Examples
- Most Popular Blogs
- Latest CISSP Exam Dumps of 2024 [Free CISSP Dumps]
- CISSP vs Security+ Certifications: Which is Best in 2024?
- Best CISSP Study Guides for 2024 + CISSP Study Plan
- How to Become an Ethical Hacker in 2024?
- Top Picks by Authors
- CISSP vs Master's Degree: Which One to Choose in 2024?
- CISSP Endorsement Process: Requirements & Example
- OSCP vs CISSP | Top Cybersecurity Certifications
- How to Pass the CISSP Exam on Your 1st Attempt in 2024?
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Picks by Authors
- Top Career Options & Courses After 12th Commerce in 2024
- Recommended Blogs
- 30 Best Answers for Your 'Reason for Job Change' in 2024
- Recommended Blogs
- Time Management Skills: How it Affects your Career
- Most Popular Blogs
- Top 28 Big Data Companies to Know in 2024
- Top Picks by Authors
- Top Big Data Tools You Need to Know in 2024
- Most Popular Blogs
- Web Development Using PHP And MySQL
- Top Picks by Authors
- Top 30 Software Engineering Projects in 2024 [Source Code]
- More
- Tutorials
- Practise Tests
- Interview Questions
- Free Courses
- Agile & PMP Practice Tests
- Agile Testing
- Agile Scrum Practice Exam
- CAPM Practice Test
- PRINCE2 Foundation Exam
- PMP Practice Exam
- Cloud Related Practice Test
- Azure Infrastructure Solutions
- AWS Solutions Architect
- AWS Developer Associate
- IT Related Pratice Test
- ITIL Practice Test
- Devops Practice Test
- TOGAF® Practice Test
- Other Practice Test
- Oracle Primavera P6 V8
- MS Project Practice Test
- Project Management & Agile
- Project Management Interview Questions
- Release Train Engineer Interview Questions
- Agile Coach Interview Questions
- Scrum Interview Questions
- IT Project Manager Interview Questions
- Cloud & Data
- Azure Databricks Interview Questions
- AWS architect Interview Questions
- Cloud Computing Interview Questions
- AWS Interview Questions
- Kubernetes Interview Questions
- Web Development
- CSS3 Free Course with Certificates
- Basics of Spring Core and MVC
- Javascript Free Course with Certificate
- React Free Course with Certificate
- Node JS Free Certification Course
- Data Science
- Python Machine Learning Course
- Python for Data Science Free Course
- NLP Free Course with Certificate
- Data Analysis Using SQL
Endpoint Security: How it Works and Its Security Components
Updated on Nov 24, 2022 | 7 min read | 8.5k views
Share:
Table of Contents
- What is Endpoint Security?
- Why Endpoint Security is Important?
- How Endpoint Protection Works?
- What’s Considered an Endpoint?
- Endpoint Protection Platforms vs. Traditional Antivirus
- Enterprise Endpoint vs Consumer Endpoint Protection
- Core Functionality of an Endpoint Protection Solution
- Advanced Endpoint Security Solutions
- Conclusion
Endpoints are a common attack path, and an attacker's goal is to not only compromise the endpoints nonetheless also gain access to the network and its valuable assets. Endpoint devices like laptops, tablets, smartphones, Point of Sale Systems (POS), Internet-of-things (IoT) gadgets, and other networking or wireless gadgets connected to business networks open attack paths for security threats.
Such attacks can be controlled with the help of Inside protection which you can learn from our course CEH course online.
What is Endpoint Security?
Endpoints security or endpoints protection is a method for securing computer networks that are remotely connected to client devices is endpoint security service.
Best Endpoint security combines proactive defense with a fresh breed of ongoing detection and reaction tools. Using cloud-based analytics prevents bloated agents from consuming valuable CPU resources, allowing employees to get their work done while businesses remain secure.
Endpoint protection systems are built to detect, analyze, block, and contain ongoing attacks. To accomplish this, they must work with other security technologies to provide administrators with visibility into advanced threats and accelerate detection and remediation response times.
Master Right Skills & Boost Your Career
Avail your free 1:1 mentorship session
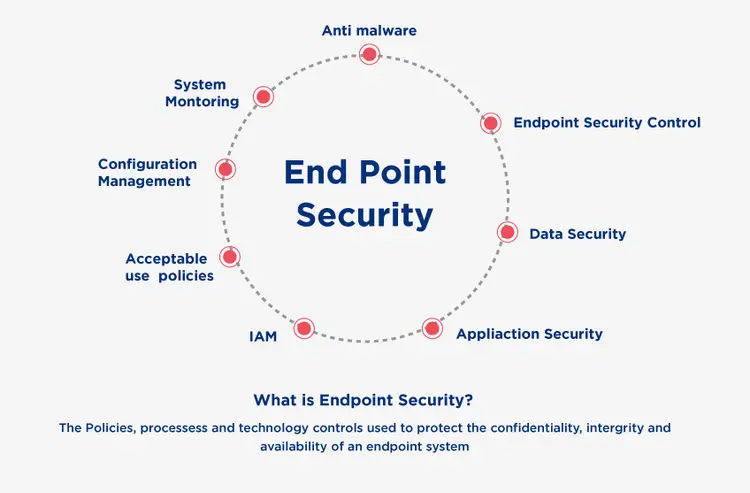
Why Endpoint Security is Important?
Endpoint security systems are crucial in today's critical situations since enterprises are being targeted regularly. Endpoint Security’s key features are follows:
1. Securing Organization’s Data
To begin with, in today's business world, data is an organization's most important asset — and losing that data, or not being able to access data, can put the entire business at risk.
2. Protecting Endpoints
Ensuring Endpoint Security is critical for Organizations as employees get connected through a wide variety of devices as well as an increasing number of endpoints. Organizations must ensure that data is secure and well-protected against misuse.
3. Securing remote work
The rise in device usage is linked to new ways of working, such as bringing your device (BYOD) and remote working policies. These policies enable employees to be as effective as possible regardless of where they are or what device they use. They do, however, make it more difficult to ensure that users are working securely, opening vulnerabilities for hackers to exploit. It is critical to secure the device with an endpoint security platform.
4. Identity protection
Employees are working virtually globally rather than in their usual office space due to Covid and contemporary hybrid working environments and connecting to organization's infrastructure via multiple devices rather than the assigned one. The significance of endpoint security in protecting company data and employee device security in today's virtually protected and connected work environment
5. Advanced Threat protection
Hackers are using more sophisticated attack methods to gain access to corporate networks, steal data, and trick employees into disclosing sensitive information. Endpoint protection is essential for modern enterprise security and for preventing cyber criminals from gaining access to their networks.
Also Read: Cyber Security Certification course
How Endpoint Protection Works?
The Main purpose of the Endpoint Protection solution is to secure networks flows and all endpoints that connect
by verifying and scanning data at the network interface, including both virtual and physical devices and associated users, with the help of a real-time cloud-based Threat Intelligence database integrated into endpoint protection.
Corporate or Comprehensive Endpoint Protection solutions provide a consolidated administration platform that helps system administrators remotely or directly monitor and configure client software on all endpoint devices. Endpoint protection solution deployed on centralized server in network.
This solution pushes software updates or threat or endpoint signatures. Endpoint security protection enables system administrators to manage security for endpoints using policy settings depending on the types of protection or web access that employees and systems require.
What’s Considered an Endpoint?
Endpoints is infrastructure that has a network interface which connects to network and can include more familiar objects like:
- Wearables such Smart Watches
- Mobile Phones
- Tablets
- Smart devices with IoT capabilities
- Laptop Computers
- Printers
- Servers
- ATMs
- Medical Equipment
- Industrial Machines
During the recent cyber-attack root cause investigation, it was discovered that one tea kettle with network access to the internet was hacked and utilized to exploit the company's network. As a result, smart watches, mobile phones, voice-controlled digital assistants, and other IoT-enabled smart gadgets are popular targets for attackers since they are often unprotected and easy access points for malicious software or viruses. Even sensors are now network-connected in our cars, aero planes, hospitals, and even oil rig drills. As different types of endpoints evolved and expanded, so did the endpoint security solutions that protected them.
Endpoint security software will typically include the following components:
- Security Threat and vulnerability protection
- Protection against security threats and vulnerabilities
- Protection against malicious software downloads
- Monitoring web browsing and help to protect safe browsing
- Proactive Malware protection
- Rapid or real-time Threat detection allows administrators to act on compromised endpoints.
- Data Loss Protection to avoid data loss by data categorization configuration.
- Protection against phishing and social engineering attacks through email
- Protection from zero-day Vulnerabilities threats and exploits in near real-time based on machine learning
- Firewall features to protect network related malicious actions.
- Platform with centralized management console to give visibility and smooth operations.
Endpoint Protection Platforms vs. Traditional Antivirus
Endpoint protection platforms (EPP) and traditional antivirus solutions differ in a number of important ways.
1. Endpoint Security vs. Network Security
Antivirus software is designed to protect a single endpoint, providing visibility into that endpoint and, in many cases, only from that endpoint. Endpoint security software, on the other hand, considers the entire enterprise network and can provide visibility into all connected endpoints from a unique location.
2. Protection
To detect viruses, traditional antivirus solutions used signature-based detection. This meant that if your company was Patient Zero, or if your users' antivirus software hadn't been updated in a while, you could still be at risk. Today's EPP solutions are automatically updated by leveraging the cloud. Additionally, previously unknown threats can be discovered using technologies such as behavioral analysis.
3. Administration
Traditionally, antivirus solutions relied on the user to manually update databases or to allow updates at predetermined times. EPPs provide interconnected security by offloading administration to the enterprise IT or cybersecurity team.
Enterprise Endpoint vs Consumer Endpoint Protection
| Enterprise Endpoint | Consumer Endpoint Protection |
| Superior at managing diverse endpoint collections | Few single-user endpoints must be managed. |
| Software for central management | Endpoints are individually installed and configured. |
| Capabilities for remote administration | Remote management is rarely required. |
| Remote device endpoint protection configuration | directly configures endpoint security on a device |
| Patches are applied to all relevant endpoints. | The user enables each device’s automatic updates. |
| Modified permissions are required. | Utilizes administrative privileges |
| Monitoring devices, activity, and behavior of employees | Activity and behavior are limited to a single user. |
Core Functionality of an Endpoint Protection Solution
Endpoint Protection solutions are often an organization's first line of defense against online threats. The functionality that Endpoint Protection solutions provide to prevent malware infections varies greatly. Some are specific and require advanced security skills to operate, and some are generic and should be included in the resource of every endpoint protection solution.
1. Prevention
NGAV - Next-Generation Antivirus (NGAV) incorporates elements like artificial intelligence, behavioral detection, machine learning algorithms, and exploit mitigation to anticipate and prevent known and unknown threats.
2. Detection: EDR
Endpoint detection and response (EDR) is an incorporated endpoint Protection solution that combines real-time continuous monitoring and endpoint data collection with rules-based automated response and analysis capabilities.
3. Managed Threat Hunting
Managed Threat Hunting combines world-class threat hunters with detection technology that runs on endpoint, network, and data sources to help you find attackers wherever they hide.
4. Threat Intelligence Integration
Threat Intelligence Integration contributes to the delivery of a new type of endpoint protection that detects potential threats during known good and bad files. Using local, global, and enterprise-level intelligence to perform an in-depth analysis of suspect files, smart execution-time decisions are made to identify and convict low-prevalence attacks and stealthy malware.
Advanced Endpoint Security Solutions
Advanced endpoint security solutions are a next-generation endpoint security solution that employs artificial intelligence (AI), machine learning (ML), and other intelligent automation capabilities to provide more comprehensive cybersecurity protection against a wide range of modern threats such as fileless malware, script-based attacks, and zero-day threats.
Must Read: KnowledgeHut CEH Course online
Conclusion
By integrating visibility, control, and proactive defense, endpoint security solutions enable businesses to strengthen the security of their devices. The cybersecurity market has many Endpoint security vendors and out of all endpoint security products, there are some top best endpoint security products are checkpoint endpoint security, Elastic endpoint security, Palo Alto endpoint, RSA Netwitness. The solution enables businesses to discover, monitor, and assess the risks posed by their endpoints, as well as ensure that all devices are compliant, mitigating potential risks, and reducing exposure. They actively defend businesses against advanced attacks. It is a critical component of cyber security tools.
Frequently Asked Questions (FAQs)
1. What is endpoint security?
2. What is an example of endpoint security?
3. How do you secure endpoints?
4. What are the types of endpoint security?
5. What are endpoint devices?
Get Free Consultation
By submitting, I accept the T&C and
Privacy Policy
