- Blog Categories
- Project Management
- Agile Management
- IT Service Management
- Cloud Computing
- Business Management
- Business Intelligence
- Quality Engineer
- Cyber Security
- Career
- Big Data
- Programming
- Most Popular Blogs
- PMP Exam Schedule for 2024: Check PMP Exam Date
- Top 60+ PMP Exam Questions and Answers for 2024
- PMP Cheat Sheet and PMP Formulas To Use in 2024
- What is PMP Process? A Complete List of 49 Processes of PMP
- Top 15+ Project Management Case Studies with Examples 2024
- Top Picks by Authors
- Top 170 Project Management Research Topics
- What is Effective Communication: Definition
- How to Create a Project Plan in Excel in 2024?
- PMP Certification Exam Eligibility in 2024 [A Complete Checklist]
- PMP Certification Fees - All Aspects of PMP Certification Fee
- Most Popular Blogs
- CSM vs PSM: Which Certification to Choose in 2024?
- How Much Does Scrum Master Certification Cost in 2024?
- CSPO vs PSPO Certification: What to Choose in 2024?
- 8 Best Scrum Master Certifications to Pursue in 2024
- Safe Agilist Exam: A Complete Study Guide 2024
- Top Picks by Authors
- SAFe vs Agile: Difference Between Scaled Agile and Agile
- Top 21 Scrum Best Practices for Efficient Agile Workflow
- 30 User Story Examples and Templates to Use in 2024
- State of Agile: Things You Need to Know
- Top 24 Career Benefits of a Certifed Scrum Master
- Most Popular Blogs
- ITIL Certification Cost in 2024 [Exam Fee & Other Expenses]
- Top 17 Required Skills for System Administrator in 2024
- How Effective Is Itil Certification for a Job Switch?
- IT Service Management (ITSM) Role and Responsibilities
- Top 25 Service Based Companies in India in 2024
- Top Picks by Authors
- What is Escalation Matrix & How Does It Work? [Types, Process]
- ITIL Service Operation: Phases, Functions, Best Practices
- 10 Best Facility Management Software in 2024
- What is Service Request Management in ITIL? Example, Steps, Tips
- An Introduction To ITIL® Exam
- Most Popular Blogs
- A Complete AWS Cheat Sheet: Important Topics Covered
- Top AWS Solution Architect Projects in 2024
- 15 Best Azure Certifications 2024: Which one to Choose?
- Top 22 Cloud Computing Project Ideas in 2024 [Source Code]
- How to Become an Azure Data Engineer? 2024 Roadmap
- Top Picks by Authors
- Top 40 IoT Project Ideas and Topics in 2024 [Source Code]
- The Future of AWS: Top Trends & Predictions in 2024
- AWS Solutions Architect vs AWS Developer [Key Differences]
- Top 20 Azure Data Engineering Projects in 2024 [Source Code]
- 25 Best Cloud Computing Tools in 2024
- Most Popular Blogs
- Company Analysis Report: Examples, Templates, Components
- 400 Trending Business Management Research Topics
- Business Analysis Body of Knowledge (BABOK): Guide
- ECBA Certification: Is it Worth it?
- How to Become Business Analyst in 2024? Step-by-Step
- Top Picks by Authors
- Top 20 Business Analytics Project in 2024 [With Source Code]
- ECBA Certification Cost Across Countries
- Top 9 Free Business Requirements Document (BRD) Templates
- Business Analyst Job Description in 2024 [Key Responsibility]
- Business Analysis Framework: Elements, Process, Techniques
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Career Options after BCom to Know in 2024
- Top 10 Power Bi Books of 2024 [Beginners to Experienced]
- Power BI Skills in Demand: How to Stand Out in the Job Market
- Top 15 Power BI Project Ideas
- Top Picks by Authors
- 10 Limitations of Power BI: You Must Know in 2024
- Top 45 Career Options After BBA in 2024 [With Salary]
- Top Power BI Dashboard Templates of 2024
- What is Power BI Used For - Practical Applications Of Power BI
- SSRS Vs Power BI - What are the Key Differences?
- Most Popular Blogs
- Data Collection Plan For Six Sigma: How to Create One?
- Quality Engineer Resume for 2024 [Examples + Tips]
- 20 Best Quality Management Certifications That Pay Well in 2024
- Six Sigma in Operations Management [A Brief Introduction]
- Top Picks by Authors
- Six Sigma Green Belt vs PMP: What's the Difference
- Quality Management: Definition, Importance, Components
- Adding Green Belt Certifications to Your Resume
- Six Sigma Green Belt in Healthcare: Concepts, Benefits and Examples
- Most Popular Blogs
- Latest CISSP Exam Dumps of 2024 [Free CISSP Dumps]
- CISSP vs Security+ Certifications: Which is Best in 2024?
- Best CISSP Study Guides for 2024 + CISSP Study Plan
- How to Become an Ethical Hacker in 2024?
- Top Picks by Authors
- CISSP vs Master's Degree: Which One to Choose in 2024?
- CISSP Endorsement Process: Requirements & Example
- OSCP vs CISSP | Top Cybersecurity Certifications
- How to Pass the CISSP Exam on Your 1st Attempt in 2024?
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Picks by Authors
- Top Career Options & Courses After 12th Commerce in 2024
- Recommended Blogs
- 30 Best Answers for Your 'Reason for Job Change' in 2024
- Recommended Blogs
- Time Management Skills: How it Affects your Career
- Most Popular Blogs
- Top 28 Big Data Companies to Know in 2024
- Top Picks by Authors
- Top Big Data Tools You Need to Know in 2024
- Most Popular Blogs
- Web Development Using PHP And MySQL
- Top Picks by Authors
- Top 30 Software Engineering Projects in 2024 [Source Code]
- More
- Tutorials
- Practise Tests
- Interview Questions
- Free Courses
- Agile & PMP Practice Tests
- Agile Testing
- Agile Scrum Practice Exam
- CAPM Practice Test
- PRINCE2 Foundation Exam
- PMP Practice Exam
- Cloud Related Practice Test
- Azure Infrastructure Solutions
- AWS Solutions Architect
- AWS Developer Associate
- IT Related Pratice Test
- ITIL Practice Test
- Devops Practice Test
- TOGAF® Practice Test
- Other Practice Test
- Oracle Primavera P6 V8
- MS Project Practice Test
- Project Management & Agile
- Project Management Interview Questions
- Release Train Engineer Interview Questions
- Agile Coach Interview Questions
- Scrum Interview Questions
- IT Project Manager Interview Questions
- Cloud & Data
- Azure Databricks Interview Questions
- AWS architect Interview Questions
- Cloud Computing Interview Questions
- AWS Interview Questions
- Kubernetes Interview Questions
- Web Development
- CSS3 Free Course with Certificates
- Basics of Spring Core and MVC
- Javascript Free Course with Certificate
- React Free Course with Certificate
- Node JS Free Certification Course
- Data Science
- Python Machine Learning Course
- Python for Data Science Free Course
- NLP Free Course with Certificate
- Data Analysis Using SQL
DNS Security: What it is and How Does it Work?
Updated on Nov 16, 2022 | 16 min read | 10.3k views
Share:
Table of Contents
- What is DNS Security?
- Importance of DNS Security
- How Does DNS Work?
- Types of DNS Security Threats
- Best Domain Name System (DNS) Security Tools
- What are Some Common Attacks Involving DNS?
- Measures Against DNS Attacks
- Best DNS Servers for Security
- Key Tips for Maintaining DNS Security
- DNS Protection Best Practices
- Conclusion
Knowing and understanding the DNS Security or Domain Name System is important before diving into DNS security solutions and DNS protections. DNS is like a contact list or traditional phone directories on the Internet. To translate domain names into IP (internet protocol) addresses, DNS maintains a directory of various domain names. DNS addresses identify every device connected to the Internet, such as a laptop, PC, iPad, or mobile phone, including the hosting server.
Recent reports indicate that almost 90% of organizations suffered DNS attacks in 2021, with each attack costing about USD 950,000 on average. Additionally, a large number of these attacks affected Indian internet users. Thus, organizations must build secure DNS servers to ensure the highest DNS cyber security. Get Ethical Hacking training online and learn more about DNS security and attack.
What is DNS Security?
Network attacks are increasingly targeting DNS. A DNS has the reputation of being one of the oldest and most relied-upon protocols on the Internet, making it a viable target for attackers. To ensure that DNS infrastructure can continue functioning quickly and reliably, it is important to use secure DNS tools to protect it against cyberattacks.
Why DNS Security is Important?
The DNS system has several design limitations, like many Internet protocols. Including spoofing, amplification, DoS (Denial of Service), or the interception of private information, these limitations, together with advancements in technology, make DNS servers vulnerable to a wide range of attacks. Therefore, organizations should handle DNS security issues carefully since it is integral to most internet requests.
Master Right Skills & Boost Your Career
Avail your free 1:1 mentorship session
Importance of DNS Security
Without DNS security, cybercriminals can easily identify security vulnerabilities and redirect a domain name to their desired location. It is unimaginable how uncomfortable it would be if we couldn’t access our company website because of an attack. The DNS threat can corrupt an online banking system and steal confidential consumer information. Thus, DNS Security is among the most critical cyber security tools, and organizations must take DNS security issues seriously.
How Does DNS Work?
Every device needs its IP address to route traffic to a connected device. The IP addresses resulting from IPv4 or IPv6 are translated to human-readable names using DNS. Similarly to a telephone number with a country code, area code, etc., the string of numbers consists of sections, including the network component, host and subnet.
Step 1: Obtaining Information About the Website
Enter the domain name into a web browser to visit a website. For instance, www.setyourwebpage.com. Upon entering the domain name, the computer will search its local DNS cache for its associated IP address. It will display websites if they are present locally. The computer will perform a DNS query if it doesn't already have the information.
Step 2: Obtain DNS Recursive Servers’ Contact Information
A computer queries another server if the information does not exist in its local cache. As with your computer, recursive DNS servers have their own local cache. Likely, common domain names are already in the cache of many ISPs who use the same recursive DNS servers. Cache-cached domains will end the query here and display the website.
Step 3: Locate Authoritative DNS Servers
DNS servers that recursively look for information elsewhere if they do not have it in their cache memory. Following that, the query is sent to the authoritative DNS servers in the chain. The search will continue until a nameserver is found for the domain. Records for domain names are stored in these authoritative name servers.
Step 4: Access DNS Record
A query to the authoritative name server will locate the IP address for www.setyourwebpage.com (A record). The authoritative name servers supply the A record to the Recursive DNS server. A local cache is then used to store the record. If another query is sent back to the recursive server, it can provide an answer to the A record for www.setyourwebpage.com. Every DNS record has an expiration date associated with it, which indicates when it will expire. After a certain period, some recursive DNS servers request updated records.
Step 5: Final Step in DNS Configuration
Your computer receives the A record from the Recursive DNS server. A local cache is then created on our computer and stored with the record. From the DNS record, it obtains the IP address and passes it on to our browser. Websites connected to A records will display this website using the web browser associated with the IP address. An entire lookup can be completed in milliseconds.
Types of DNS Security Threats
1. Typosquatting
Social engineering attacks such as typosquatting target internet users who type URLs incorrectly. For instance, the attacker requested to click on https://www.aplle.com/ instead of https://www.apple.com. When URLs misspell the original/authentic websites, users are typically tricked into visiting malicious websites. These fake sites trick users into entering sensitive information and have the potential to do significant damage to organizations by stealing sensitive information.
2. Distributed Denial of Service Attacks (DDoS)
Multiple connected online devices, collectively known as botnets, are used in DDoS attacks to overwhelm a target website.
3. DNS Cache Poisoning
Users are sent to the wrong website due to DNS cache poisoning, which creates incorrect DNS responses and inaccurate DNS cache entries.
4. DNS Amplification
In DNS Amplification, attackers amplify their traffic using open DNS resolver functionality to dominate a target server or network with a large traffic volume, thereby rendering it inaccessible to the attacker. This is an effective distributed reflection-based DDoS (denial-of-service) attack.
Best Domain Name System (DNS) Security Tools
DNS security tools are designed to prevent cyber attacks by acting as an intermediary between the web browser and the websites the user is trying to access online. In addition to securing public DNS, its security tools eliminate botnet servers, filter content such as advertising or adult websites and fix typos in domain names. Below are the top six best DNS security tools to use:
1. Cisco Umbrella
Cisco Umbrella offers DNS security tools through its cloud server. A single DNS solution integrates multiple security functions, protecting devices, remote users, and distributed locations. It takes minutes to install the Cisco Umbrella DNS security tool and secure the user's data to max level. Cisco Umbrella reports provide information about the activity of each device or network within the system.
2. TitanHQ WebTitan
In terms of protecting against web-based cyber threats such as malicious websites, malware, or ransomware, TitanHQ Web Filter stands out among DNS-based security solutions. Global enterprises trust TitanHQ Web Filter because its API set allows for advanced control over web and DNS filtering, allowing them to filter web traffic and DNS traffic. Additionally, the system provides real-time automated detection and blocking of malicious threats.
3. Infoblox BloxOne Threat Defense
In addition to detecting risks, Infoblox BloxOne Threat Defense helps you prevent attacks early in their lifecycle. This solution enhances security stack effectiveness, safeguards digital operations, and lowers cybersecurity costs by integrating universal automation and ecosystems. Infoblox BloxOne Threat Defense includes DNS protection tools to help users protect their systems in hybrid workplaces with visibility, command, and automation.
4. F5 BIG-IP DNS
F5 BIG-IP DNS distributes DNS and application requests according to company regulations and data center and cloud service conditions, as well as the user's location and performance. As a complete proxy, F5 BIG-IP DNS can be configured across architectures and globally to supply global server load balancing for applications and DNS.
5. Palo Alto Networks DNS Security
The user can automatically prevent phishing attacks by enabling URL Filtering in Palo Alto Networks DNS security, including links in online ads, emails, SMS links, websites, HTTP-based command and control, and malicious sites. Palo Alto Networks DNS security is a great pick for SMEs (small-medium enterprises).
6. Infoblox Advanced DNS Protection
The Infoblox ADP blocks various attacks, including DNS hijackings, volumetric attacks and NXDOMAINs. In addition to detecting and mitigating DNS attacks, The Infoblox ADP does not require security patches because it uses constantly updated threat intelligence.
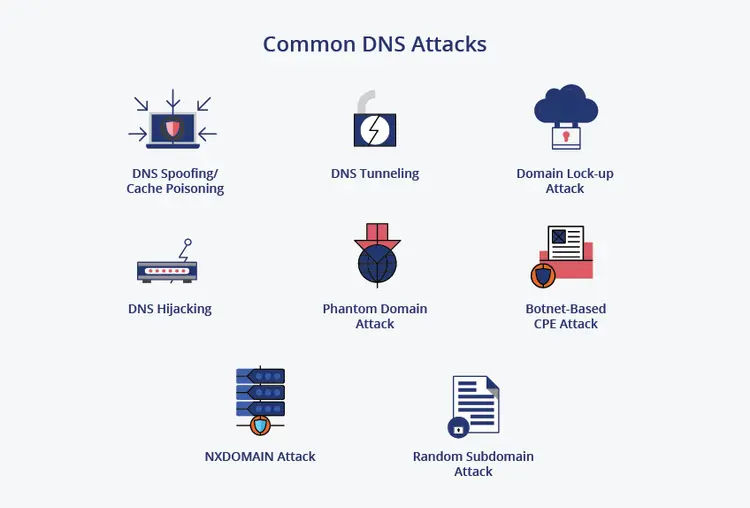
What are Some Common Attacks Involving DNS?
1. DNS Spoofing/Cache Poisoning
The DNS cache poisoning method is also called DNS spoofing. The purpose of DNS spoofing is to redirect organic traffic from a legitimate server to a fake server by exploiting vulnerabilities in the DNS.
2. DNS Tunnelling
In most organizations, DNS is used freely within and outside their networks since it is considered a trusted protocol. Cyber crooks exploit DNS for data exfiltration using malware that contains the data being exfiltrated in DNS requests. Attackers ensure that the data users are transmitting in the DNS response packet reaches a server controlled by them, not by the website owner.
3. DNS Hijacking
Users are fooled into believing they are connected to a legitimate domain when they are connected to a malicious one by DNS hijackers. DNS servers can be compromised to store incorrect data by using malicious or compromised DNS servers.
4. NXDOMAIN Attack
Clients are prevented from accessing the roadmap through the DNS NXDOMAIN flood attack. DNS servers are swamped with invalid or nonexistent requests when this attack occurs.
5. Phantom Domain Attack
Phantom domain attacks are types of DoS attacks that target authoritative nameservers. An attack is conducted by setting up several DNS servers that fail to respond to DNS requests or do so sluggishly, disrupting communication.
To find an IP address, a DNS server searches the addresses of other DNS servers connected to it; this process is known as recursive DNS. Attacks against phantom domains result in inefficient lookups or non-functional searches and waste of server resources.
When recursive DNS servers fully consume resources, they can cause serious performance problems by ignoring legitimate queries and focusing on non-responsive servers.
6. Random Subdomain Attack
Random subdomain attacks are similar to NXDOMAIN attacks except that they ask for nonexistent subdomains instead of nonexistent domains.
7. Domain Lock-up Attack
A DNS resolver is locked up by these attacks, as their name implies. This is accomplished by connecting to a resolver with TCP, and then allowing domains to send randomly generated junk packets, which overwhelm a resolver.
8. Botnet-based CPE Attack
These attacks are developed by exploiting devices such as modems, routers, cable boxes, etc., used as CPE (Customer Premise Equipment). The attackers compromise CPEs, and the devices are made part of a botnet that attacks one or more sites or domains at random.
Measures Against DNS Attacks
- One can protect private data with digital signatures and certificates.
- One should do a DNS zone review regularly. It's easy to forget about checking domain names or subdomains that may run outdated software or expose unrestricted areas to attackers as time goes on.
- To ensure that the A, CNAME, and MX records are accurate, reviewing all your zones, records, IPs, and SSL certificates is crucial.
- Make sure to use the latest Hide BIND version software. Several features are available in BIND, including DNSSEC, DNSTAP, Scaleable Primary-Secondary Hierarchy, Minimal ANY Responses, and many more. Major DNS servers on the Internet use BIND software.
- Maintain regular software check-ups and fix faulty bugs as soon as they arise.
- Make backups of data on different servers; in case of corruption or loss on one server, other servers can restore the data.
- Ensure the data centers are connected to various networks; it helps in reducing the risk of single-point failures.
- Ensure that your DNS configuration is as secure as possible. The domain names that need to be resolved can be randomly cased, and one can randomly generate the query ID instead of the standard DNS port.
Best DNS Servers for Security
You can improve and use secure dynamic DNS by switching DNS providers. With so many things on the Internet involving DNS requests, choosing the fastest DNS directory across all your devices and securing public DNS will allow you to do almost everything faster. The top three recommended best DNS servers enhance your online security.
1. Cloudflare DNS
There is no doubt that Cloudflare DNS is an excellent DNS protection service worldwide. Newly, Cloudfare DNS built 1.1.1.1, the fastest DNS service globally.
You cannot restrict what websites you visit with Cloudflare DNS protection, but your privacy comes first. Cloudflare does not log your DNS traffic or your IP address. The Cloudflare DNS filtering automatically deletes everything logged within 24 hours. Thus, Cloudfare DNS makes the best choice among many enterprises. Recently, in response to a massive DDoS attack against Minecraft, Cloudflare mitigated the damage.
2. OpenDNS
A popular DNS server offers free, public, web-based DNS servers. Open DNS is a popular choice among many enterprises and is used by millions of people. Cisco has owned OpenDNS since 2016.
When it comes to protecting yourself from malicious attacks, OpenDNS is a reliable choice. You can speed up page loading by connecting to the nearest DNS server through anycast routing. In addition to high-speed internet transfer, OpenDNS also blocks phishing websites, filters adult web content, and records your online activity for a year.
OpenDNS offers three services in their Home package, two of which are free: OpenDNS Family Shield and OpenDNS Home. Aside from not recording internet activity history and not providing access to specific websites, it offers all the same features as the paid version.
3. Google Public DNS
The speed of Google DNS is its greatest advantage. In addition to global coverage, Google DNS is DNSSEC-encrypted as standard; it has load balancing and shared caching to improve cache hit rates. Using Google Public DNS will make your browsing experience faster and more secure, and you won’t be redirected.
Key Tips for Maintaining DNS Security
1. DNS Security Extensions or DNSSEC
A pair of public keys is attached to every DNS zone and digital signatures are generated over DNS data using the owner’s key. Keeping this key material secured is the responsibility of the owner.
In DNSSEC, private key cryptography strengthens authentication through digital signatures. DNSSEC does not cryptographically sign DNS queries or responses but rather certificates that certify DNS data directly from the owner.
2. Encrypting Data
The encryption of data included in DNS requests and responses provides an enhanced level of security. A layer of security can be provided by encrypting data to prevent hackers from intercepting or inserting malware.
3. Implementing Secure DNS Configurations
DNS servers can be configured in a secret vault without being connected to other DNS servers inside an organization. As a result, two DNS servers cannot establish a connection with each other. It is, therefore, unlikely that other servers will be affected if one server is compromised.
Furthermore, limiting the amount of data that is stored on each server can be achieved with secure DNS configurations. An encrypted configuration helps prevent data from being compromised on a broader scale.
4. Running Regular System Updates
Updates to DNS servers are scheduled regularly. Keeping these updates up-to-date is crucial. These updates introduce new security protocols that enable the servers to identify and fix vulnerabilities before they impact other systems.
5. Strengthening Detection Protocols
Increased DNS activity about a particular domain from a single source is a critical warning sign of malicious activity. In addition, the number of domain names encountered by one source can increase when there is an attempt to enter the DNS server for spoofing. Thus, monitoring and preventing malware attacks requires strong detection protocols.
6. Security Training
DNS servers require robust security training, which is mandatory in most organizations today. Using safe practices when interacting with the internet becomes easier for users when they know the potential risks. One should include several key techniques in training:
- Checking the SSL (Secure Sockets Layer) or TLS (Transport Layer Security certificates) of websites you access.
- Be cautious when clicking unrecognized links.
- Run security checks as soon as the system requests them. One should not delay the process. Delay makes the system more vulnerable.
7. What is DNS over HTTPS?
DoH (Domain Name System (DNS) over HTTPS) encrypts DNS traffic within an HTTPS session by passing DNS requests through an encrypted HTTP session. By hiding DNS queries from view, DoH seeks to protect online privacy.
The DoH protocol works similarly to DNS, except requests are maintained by HTTPS sessions. This helps in reducing the amount of information passed between the user and the server. The encrypted data over HTTP protocol is supported by many web browsers, including Google Chrome, Microsoft Edge, and Mozilla Firefox, as part of their efforts to enhance data privacy and security.
If you wish to enhance and boost your cyber security knowledge, then you must go for IT Security certification courses.
DNS Protection Best Practices
DNS security practices are essential for all organizations due to DNS’s increasing importance in nearly all networked applications. A networked application can communicate easily with another with its help.
1. Enable DNS Logging
Businesses can protect their DNS servers from attackers by enabling log information for DNS activities. One can comprehensively track DNS events and activity using this strategy.
2. Lock DNS Cache
If the DNS server receives a request, it usually caches that information for future use to answer the request quickly the next time. DNS caching, however, can be dangerous because attackers can alter the cached information. Preventing unauthorized changes to cached details requires locking them from unauthorized access. Administrators can decide when to update and scrutinize cached data. In DNS, the lookup information is only stored for a specified period based on the time-to-live setting.
3. Filter DNS Requests to Block Malicious Domains
In addition to keeping malware off company networks and user devices, DNS filtering will protect corporate networks from spreading malicious software. Additionally, DNS filtering can block domains hosting forbidden or inappropriate content, but not necessarily those used for malware or phishing attacks.
4. Validate DNS Data Integrity with DNSSEC
DNSSEC is an extension of the Domain Name System that allows businesses to evaluate queries for authenticity and send only validated ones. Digitally signing DNS data is another way to ensure its integrity, which DNSSEC does.
The DNS server checks the signatures from DNSSEC when DNSSEC is installed. Validation and identification of the signature are required. DNSSEC provides integrity of shared data and its origin to protect companies from DNS spoofing and cache poisoning.
5. Configure Access Control Lists
The most reliable way to prevent attacks on primary DNS servers is to control access to them with an Access Control List. IT and system administrators should restrict access to the primary DNS server. Furthermore, the list must specify which servers are authorized to transfer zones. Attackers may push zone transfer queries via secondary DNS servers to gain access to the server. Cybercriminals cannot access zone information or data if they have an adequate ACL and zone transfer allocation.
Looking to boost your ITIL skills? Our ITIL specialist courses offer the perfect opportunity to enhance your knowledge and advance your career. Join us today and become an ITIL expert!
Conclusion
Unfathomable amounts of information can be found on the internet, but it has also brought cyber attackers into the picture. Whenever you browse online, one mistake can make you a victim of malware or phishing. To protect themselves against cybercrime, enterprises are increasingly using DNS security software. Learn cybersecurity protection techniques with KnowledgeHut Ethical Hacking training.
Frequently Asked Questions (FAQs)
1. What is DNS and its purpose?
2. Can DNS steal data?
3. Who hosts DNS servers?
Get Free Consultation
By submitting, I accept the T&C and
Privacy Policy
