- Blog Categories
- Project Management
- Agile Management
- IT Service Management
- Cloud Computing
- Business Management
- Business Intelligence
- Quality Engineer
- Cyber Security
- Career
- Big Data
- Programming
- Most Popular Blogs
- PMP Exam Schedule for 2024: Check PMP Exam Date
- Top 60+ PMP Exam Questions and Answers for 2024
- PMP Cheat Sheet and PMP Formulas To Use in 2024
- What is PMP Process? A Complete List of 49 Processes of PMP
- Top 15+ Project Management Case Studies with Examples 2024
- Top Picks by Authors
- Top 170 Project Management Research Topics
- What is Effective Communication: Definition
- How to Create a Project Plan in Excel in 2024?
- PMP Certification Exam Eligibility in 2024 [A Complete Checklist]
- PMP Certification Fees - All Aspects of PMP Certification Fee
- Most Popular Blogs
- CSM vs PSM: Which Certification to Choose in 2024?
- How Much Does Scrum Master Certification Cost in 2024?
- CSPO vs PSPO Certification: What to Choose in 2024?
- 8 Best Scrum Master Certifications to Pursue in 2024
- Safe Agilist Exam: A Complete Study Guide 2024
- Top Picks by Authors
- SAFe vs Agile: Difference Between Scaled Agile and Agile
- Top 21 Scrum Best Practices for Efficient Agile Workflow
- 30 User Story Examples and Templates to Use in 2024
- State of Agile: Things You Need to Know
- Top 24 Career Benefits of a Certifed Scrum Master
- Most Popular Blogs
- ITIL Certification Cost in 2024 [Exam Fee & Other Expenses]
- Top 17 Required Skills for System Administrator in 2024
- How Effective Is Itil Certification for a Job Switch?
- IT Service Management (ITSM) Role and Responsibilities
- Top 25 Service Based Companies in India in 2024
- Top Picks by Authors
- What is Escalation Matrix & How Does It Work? [Types, Process]
- ITIL Service Operation: Phases, Functions, Best Practices
- 10 Best Facility Management Software in 2024
- What is Service Request Management in ITIL? Example, Steps, Tips
- An Introduction To ITIL® Exam
- Most Popular Blogs
- A Complete AWS Cheat Sheet: Important Topics Covered
- Top AWS Solution Architect Projects in 2024
- 15 Best Azure Certifications 2024: Which one to Choose?
- Top 22 Cloud Computing Project Ideas in 2024 [Source Code]
- How to Become an Azure Data Engineer? 2024 Roadmap
- Top Picks by Authors
- Top 40 IoT Project Ideas and Topics in 2024 [Source Code]
- The Future of AWS: Top Trends & Predictions in 2024
- AWS Solutions Architect vs AWS Developer [Key Differences]
- Top 20 Azure Data Engineering Projects in 2024 [Source Code]
- 25 Best Cloud Computing Tools in 2024
- Most Popular Blogs
- Company Analysis Report: Examples, Templates, Components
- 400 Trending Business Management Research Topics
- Business Analysis Body of Knowledge (BABOK): Guide
- ECBA Certification: Is it Worth it?
- How to Become Business Analyst in 2024? Step-by-Step
- Top Picks by Authors
- Top 20 Business Analytics Project in 2024 [With Source Code]
- ECBA Certification Cost Across Countries
- Top 9 Free Business Requirements Document (BRD) Templates
- Business Analyst Job Description in 2024 [Key Responsibility]
- Business Analysis Framework: Elements, Process, Techniques
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Career Options after BCom to Know in 2024
- Top 10 Power Bi Books of 2024 [Beginners to Experienced]
- Power BI Skills in Demand: How to Stand Out in the Job Market
- Top 15 Power BI Project Ideas
- Top Picks by Authors
- 10 Limitations of Power BI: You Must Know in 2024
- Top 45 Career Options After BBA in 2024 [With Salary]
- Top Power BI Dashboard Templates of 2024
- What is Power BI Used For - Practical Applications Of Power BI
- SSRS Vs Power BI - What are the Key Differences?
- Most Popular Blogs
- Data Collection Plan For Six Sigma: How to Create One?
- Quality Engineer Resume for 2024 [Examples + Tips]
- 20 Best Quality Management Certifications That Pay Well in 2024
- Six Sigma in Operations Management [A Brief Introduction]
- Top Picks by Authors
- Six Sigma Green Belt vs PMP: What's the Difference
- Quality Management: Definition, Importance, Components
- Adding Green Belt Certifications to Your Resume
- Six Sigma Green Belt in Healthcare: Concepts, Benefits and Examples
- Most Popular Blogs
- Latest CISSP Exam Dumps of 2024 [Free CISSP Dumps]
- CISSP vs Security+ Certifications: Which is Best in 2024?
- Best CISSP Study Guides for 2024 + CISSP Study Plan
- How to Become an Ethical Hacker in 2024?
- Top Picks by Authors
- CISSP vs Master's Degree: Which One to Choose in 2024?
- CISSP Endorsement Process: Requirements & Example
- OSCP vs CISSP | Top Cybersecurity Certifications
- How to Pass the CISSP Exam on Your 1st Attempt in 2024?
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Picks by Authors
- Top Career Options & Courses After 12th Commerce in 2024
- Recommended Blogs
- 30 Best Answers for Your 'Reason for Job Change' in 2024
- Recommended Blogs
- Time Management Skills: How it Affects your Career
- Most Popular Blogs
- Top 28 Big Data Companies to Know in 2024
- Top Picks by Authors
- Top Big Data Tools You Need to Know in 2024
- Most Popular Blogs
- Web Development Using PHP And MySQL
- Top Picks by Authors
- Top 30 Software Engineering Projects in 2024 [Source Code]
- More
- Tutorials
- Practise Tests
- Interview Questions
- Free Courses
- Agile & PMP Practice Tests
- Agile Testing
- Agile Scrum Practice Exam
- CAPM Practice Test
- PRINCE2 Foundation Exam
- PMP Practice Exam
- Cloud Related Practice Test
- Azure Infrastructure Solutions
- AWS Solutions Architect
- AWS Developer Associate
- IT Related Pratice Test
- ITIL Practice Test
- Devops Practice Test
- TOGAF® Practice Test
- Other Practice Test
- Oracle Primavera P6 V8
- MS Project Practice Test
- Project Management & Agile
- Project Management Interview Questions
- Release Train Engineer Interview Questions
- Agile Coach Interview Questions
- Scrum Interview Questions
- IT Project Manager Interview Questions
- Cloud & Data
- Azure Databricks Interview Questions
- AWS architect Interview Questions
- Cloud Computing Interview Questions
- AWS Interview Questions
- Kubernetes Interview Questions
- Web Development
- CSS3 Free Course with Certificates
- Basics of Spring Core and MVC
- Javascript Free Course with Certificate
- React Free Course with Certificate
- Node JS Free Certification Course
- Data Science
- Python Machine Learning Course
- Python for Data Science Free Course
- NLP Free Course with Certificate
- Data Analysis Using SQL
- Home
- Blog
- It Service Management
- Who is an Information Security Manager? Let’s explore!
Who is an Information Security Manager? Let’s explore!
Updated on Mar 21, 2024 | 4 min read | 1.1k views
Share:
Table of Contents
- Who is an Information Security Manager?
- What Does an Information Security Manager Do? [Roles and Responsibilities]
- Characteristics of an Effective Information Security Manager
- Qualifications and Required Skills of Information Security Manager
- Information Security Manager: Education, Training and Certifications
- Information Security Manager Careers
- How to Become an Information Security Manager?
- Information Security Manager Salary and Job Growth
- Conclusion
The Internet and computers have become significant assets for humanity today. From online banking to job applications, dependence on these digital tools has surged in the last decade. However, with the power of the Internet comes a substantial responsibility to safeguard all the data stored on our systems. This is where the information security manager steps into the picture. So, who is an information security manager?
Since I entered the tech era in 2000, I have witnessed the evolution of the profile of information security managers.
Throughout my experience in the industry, several aspirants have opted for ITIL Course online to pursue a career path. However, many of them need to realize the importance of exploring career opportunities.
Do you want to know who is an information security manager? Let me guide you in learning all about these professionals and your potential career in this dynamic field!
Who is an Information Security Manager?
Information security managers are responsible for protecting an organization's databases, networks, and computer systems against digital attacks and security lapses.
The information security manager job description requires you to utilize your expertise and make intelligent decisions. The job profile focuses on proactively establishing defenses against threats and responding efficiently to security breaches.
What Does an Information Security Manager Do? [Roles and Responsibilities]
When I entered the field as an entry-level professional, I realized duties might vary depending on the exact job profile. Here are some key information security manager roles and responsibilities.
- Monitoring Network and Infrastructure: You will be responsible for regularly assessing logs to identify suspicious activity and maintaining an organization's data systems and networks.
- Building Strategy and Audits: You must coordinate with the team to develop strategies for security audits and protocols. You should also conduct a forensic investigation during the breach to assess the system's strengths and weaknesses.
- Implementing New Technology: As an Information Security Manager, you are responsible for overseeing the incorporation of any new technology. You need to ensure that both software and hardware systems are secured to prevent vulnerabilities in the existing network.
Characteristics of an Effective Information Security Manager
In my field experience, I have realized that to emerge as a proficient information security manager, one should possess additional characteristics. Here are some of them:
- Being prepared: A skilled information security manager should be prepared for any unforeseeable event.
- Being knowledgeable: It's crucial to understand the ins and outs of security requirements.
- Having moral courage: This involves doing what is right for the business and employees.
- Having strong communication skills: Effective communication ensures that you are making the right choices.
Qualifications and Required Skills of Information Security Manager
I have explained who is an information security manager. Now, let's explore the qualifications and required skills. As a basic qualification, you need to have at least a bachelor’s degree in information security or an IT-related discipline. Other organizations might also require a master’s degree in an information security-related domain, even with a non-technical bachelor’s program.
On the other hand, I have also listed the information security manager skills.
- Risk management: As an information security manager, you should plan a systematic approach to identifying, assessing, and mitigating potential risks.
- Incident response: Security managers should use incident response strategies to protect their organization from security threats while coordinating and supervising actions.
- Communication: The information security manager should act as a focal point of communication between the team and the organization. They should be fluent in or open to communication with other department managers.
- Analytical skills: In this demanding role, professionals should possess analytical skills to analyze security issues and provide effective resolutions quickly.
- Adaptability: The role of the information security manager involves a high-level understanding and quick adaptation for successful resolution.
Information Security Manager: Education, Training and Certifications
Now that you know who is an information security manager, it's time to learn about their basic qualifications. To qualify for a career as an information security manager, follow the steps below.
Education
When learning about who is an information security manager, you may have encountered the fundamental qualifications for the role. Most employers require a strong educational background for information security professionals. The conventional way to achieve this is by completing a bachelor's degree. A bachelor's in computer science, IT, or a relevant field serves as a foundation for your career in the industry.
Training
Another option that aspirants have today is training and workshops. Enrolling in a streamlined course involves who is an information security manager and takes learners from novices to job-ready experts. The advantage of training is that your learning will be more focused and contribute to upskilling individuals with the latest resources.
Certifications
Individuals often pursue specialization and certification courses to enhance their eligibility. Programs like CISSP, CISM, and CEH are highly sought-after credentials in the field. By obtaining the relevant program, you can bolster your credentials and demonstrate your commitment to the field.
- CISSP - Certified Information Security Professional program validates your knowledge in designing, implementing, and managing a cybersecurity program. The certification has an excellent technical scope and regulates the day-to-day operations of a business.
- CISM - Certified Information Security Manager focuses on the strategic goals and security features of an organization. The course validates your skills related to security management responsibilities.
- KnowledgeHut- I often recommend aspirants opt for courses in IT Service Management. This will enhance their skills related to information security management through experiential learning, making them more competitive for managerial roles.
Information Security Manager Careers
The career progression after learning who an information security manager is involves a series of steps with increasing levels of responsibilities. Here are some of the job titles.
- Entry-level security analyst: You have to start your professional journey in the information security career with entry-level roles. This job title provides hands-on experience in different aspects of information security and lays the foundation for future growth.
- Security Engineer/Consultant: In the next step, you will be exposed to working on more complex projects as a security consultant. As you know who an information security manager is, you will gain experience conducting security assessments and contribute to developing effective strategies.
- Information security manager: In these primary positions, you manage security programs, policies, and initiatives. You should also collaborate with stakeholders, lead security teams, and ensure compliance with regulations.
- Chief Information Security Officer (CISO): The CISO is responsible for protecting the company’s information security strategy, programs, and policies.
How to Become an Information Security Manager?
Now that you have learned who is an information security manager, let’s explore how to become one. Here, I have created a step-by-step guide.
- Learn the right tools: Information security requires the use of a wide range of tools. For functions such as virus detection and vulnerability management, learn how to operate with tools like Spybot, Atera, or Quarts.
- Build practical experience: Exposure to a practical environment will help you learn security strategies for dealing with digital threats.
- Find a mentor: Mentors can help you understand how the industry works. My mentor, who was my peer in the industry, has guided me based on my goals. Ensure that you have a good rapport with them to build a long-term relationship.
- Consider a Master’s degree: Having the relevant information security manager skills is extremely important. However, obtaining an advanced degree will enhance your qualifications and provide a strong background during interviews.
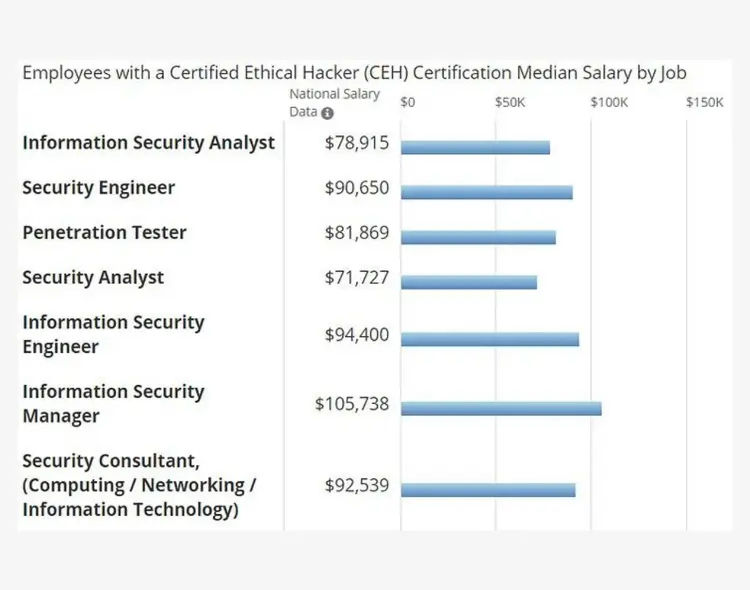
Information Security Manager Salary and Job Growth
There’s never been a better time to begin your information security manager career. Let's have an overview of the salary aspects of an information security manager.
| Country | Average Salary (Source: Glassdoor) |
| India | INR 10,00,000 – 24,00,000 |
| US | $181,000 - $294,000 |
| UK | £53000 - £81000 |
| Australia | AUD 125,000 – AUD 163,000 |
| Canada | CAD 99,000 – CAD 137,000 |
| Singapore | SGD 7000 – SGD 13000 |
| Company | Average Salary (Source: Glassdoor) |
| Accenture | $183,849/yr |
| Apple | $348,264/yr |
| Intel Corporation | $234,853/yr |
| Oracle | $237,075/yr |
| Paypal | $245,126/yr |
| Walt Disney | $146,110/yr |
| Meta | $245,070/yr |
Master Right Skills & Boost Your Career
Avail your free 1:1 mentorship session
medium
Job Overlook
A report from ISC indicates that there is a need for 4 million security professionals for their workforce. And let me assure you, the salaries for professionals are quite lucrative when you reach the managerial level. According to Cyberseek’s data, 12% of cybersecurity managers have an associate degree, 67% have a bachelor's, and 21% have pursued a master’s degree. The figures emphasize the fact that choosing your career as an information security manager will get you a lucrative future.
Conclusion
The information security manager's responsibilities are vital to any organization in today’s modern era. With the ever-increasing threat rate of cyber attacks, it is critical to have someone in this pivotal role who possesses the necessary knowledge and stays updated on the latest security trends and technologies.
If you are one of those ambitious individuals who want to begin an information security manager career, I recommend you enroll in the KnowledgeHut ITIL course online. This program helps you gain essential skills and enables you to have a solid grasp of security technologies, fostering the ability to work seamlessly in a fast-paced environment.
Frequently Asked Questions (FAQs)
1. What is the average salary of an Information Security Manager?
2. How is an Information Security Manager different from a Cybersecurity Analyst?
3. What industries need Information Security Managers?
4. How does an Information Security Manager stay updated with the latest security threats?
Get Free Consultation
By submitting, I accept the T&C and
Privacy Policy
