- Blog Categories
- Project Management
- Agile Management
- IT Service Management
- Cloud Computing
- Business Management
- Business Intelligence
- Quality Engineer
- Cyber Security
- Career
- Big Data
- Programming
- Most Popular Blogs
- PMP Exam Schedule for 2024: Check PMP Exam Date
- Top 60+ PMP Exam Questions and Answers for 2024
- PMP Cheat Sheet and PMP Formulas To Use in 2024
- What is PMP Process? A Complete List of 49 Processes of PMP
- Top 15+ Project Management Case Studies with Examples 2024
- Top Picks by Authors
- Top 170 Project Management Research Topics
- What is Effective Communication: Definition
- How to Create a Project Plan in Excel in 2024?
- PMP Certification Exam Eligibility in 2024 [A Complete Checklist]
- PMP Certification Fees - All Aspects of PMP Certification Fee
- Most Popular Blogs
- CSM vs PSM: Which Certification to Choose in 2024?
- How Much Does Scrum Master Certification Cost in 2024?
- CSPO vs PSPO Certification: What to Choose in 2024?
- 8 Best Scrum Master Certifications to Pursue in 2024
- Safe Agilist Exam: A Complete Study Guide 2024
- Top Picks by Authors
- SAFe vs Agile: Difference Between Scaled Agile and Agile
- Top 21 Scrum Best Practices for Efficient Agile Workflow
- 30 User Story Examples and Templates to Use in 2024
- State of Agile: Things You Need to Know
- Top 24 Career Benefits of a Certifed Scrum Master
- Most Popular Blogs
- ITIL Certification Cost in 2024 [Exam Fee & Other Expenses]
- Top 17 Required Skills for System Administrator in 2024
- How Effective Is Itil Certification for a Job Switch?
- IT Service Management (ITSM) Role and Responsibilities
- Top 25 Service Based Companies in India in 2024
- Top Picks by Authors
- What is Escalation Matrix & How Does It Work? [Types, Process]
- ITIL Service Operation: Phases, Functions, Best Practices
- 10 Best Facility Management Software in 2024
- What is Service Request Management in ITIL? Example, Steps, Tips
- An Introduction To ITIL® Exam
- Most Popular Blogs
- A Complete AWS Cheat Sheet: Important Topics Covered
- Top AWS Solution Architect Projects in 2024
- 15 Best Azure Certifications 2024: Which one to Choose?
- Top 22 Cloud Computing Project Ideas in 2024 [Source Code]
- How to Become an Azure Data Engineer? 2024 Roadmap
- Top Picks by Authors
- Top 40 IoT Project Ideas and Topics in 2024 [Source Code]
- The Future of AWS: Top Trends & Predictions in 2024
- AWS Solutions Architect vs AWS Developer [Key Differences]
- Top 20 Azure Data Engineering Projects in 2024 [Source Code]
- 25 Best Cloud Computing Tools in 2024
- Most Popular Blogs
- Company Analysis Report: Examples, Templates, Components
- 400 Trending Business Management Research Topics
- Business Analysis Body of Knowledge (BABOK): Guide
- ECBA Certification: Is it Worth it?
- How to Become Business Analyst in 2024? Step-by-Step
- Top Picks by Authors
- Top 20 Business Analytics Project in 2024 [With Source Code]
- ECBA Certification Cost Across Countries
- Top 9 Free Business Requirements Document (BRD) Templates
- Business Analyst Job Description in 2024 [Key Responsibility]
- Business Analysis Framework: Elements, Process, Techniques
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Career Options after BCom to Know in 2024
- Top 10 Power Bi Books of 2024 [Beginners to Experienced]
- Power BI Skills in Demand: How to Stand Out in the Job Market
- Top 15 Power BI Project Ideas
- Top Picks by Authors
- 10 Limitations of Power BI: You Must Know in 2024
- Top 45 Career Options After BBA in 2024 [With Salary]
- Top Power BI Dashboard Templates of 2024
- What is Power BI Used For - Practical Applications Of Power BI
- SSRS Vs Power BI - What are the Key Differences?
- Most Popular Blogs
- Data Collection Plan For Six Sigma: How to Create One?
- Quality Engineer Resume for 2024 [Examples + Tips]
- 20 Best Quality Management Certifications That Pay Well in 2024
- Six Sigma in Operations Management [A Brief Introduction]
- Top Picks by Authors
- Six Sigma Green Belt vs PMP: What's the Difference
- Quality Management: Definition, Importance, Components
- Adding Green Belt Certifications to Your Resume
- Six Sigma Green Belt in Healthcare: Concepts, Benefits and Examples
- Most Popular Blogs
- Latest CISSP Exam Dumps of 2024 [Free CISSP Dumps]
- CISSP vs Security+ Certifications: Which is Best in 2024?
- Best CISSP Study Guides for 2024 + CISSP Study Plan
- How to Become an Ethical Hacker in 2024?
- Top Picks by Authors
- CISSP vs Master's Degree: Which One to Choose in 2024?
- CISSP Endorsement Process: Requirements & Example
- OSCP vs CISSP | Top Cybersecurity Certifications
- How to Pass the CISSP Exam on Your 1st Attempt in 2024?
- Most Popular Blogs
- Best Career options after BA [2024]
- Top Picks by Authors
- Top Career Options & Courses After 12th Commerce in 2024
- Recommended Blogs
- 30 Best Answers for Your 'Reason for Job Change' in 2024
- Recommended Blogs
- Time Management Skills: How it Affects your Career
- Most Popular Blogs
- Top 28 Big Data Companies to Know in 2024
- Top Picks by Authors
- Top Big Data Tools You Need to Know in 2024
- Most Popular Blogs
- Web Development Using PHP And MySQL
- Top Picks by Authors
- Top 30 Software Engineering Projects in 2024 [Source Code]
- More
- Tutorials
- Practise Tests
- Interview Questions
- Free Courses
- Agile & PMP Practice Tests
- Agile Testing
- Agile Scrum Practice Exam
- CAPM Practice Test
- PRINCE2 Foundation Exam
- PMP Practice Exam
- Cloud Related Practice Test
- Azure Infrastructure Solutions
- AWS Solutions Architect
- AWS Developer Associate
- IT Related Pratice Test
- ITIL Practice Test
- Devops Practice Test
- TOGAF® Practice Test
- Other Practice Test
- Oracle Primavera P6 V8
- MS Project Practice Test
- Project Management & Agile
- Project Management Interview Questions
- Release Train Engineer Interview Questions
- Agile Coach Interview Questions
- Scrum Interview Questions
- IT Project Manager Interview Questions
- Cloud & Data
- Azure Databricks Interview Questions
- AWS architect Interview Questions
- Cloud Computing Interview Questions
- AWS Interview Questions
- Kubernetes Interview Questions
- Web Development
- CSS3 Free Course with Certificates
- Basics of Spring Core and MVC
- Javascript Free Course with Certificate
- React Free Course with Certificate
- Node JS Free Certification Course
- Data Science
- Python Machine Learning Course
- Python for Data Science Free Course
- NLP Free Course with Certificate
- Data Analysis Using SQL
What is the Importance of Cyber Security?
Updated on Oct 30, 2022 | 16 min read | 43.5k views
Share:
Table of Contents
- What is Cyber Security and Why is it Important?
- Why is it Important to Learn about Cybersecurity?
- Importance of Cyber Security in the Digital World
- Importance of Cyber Security for Students
- Importance of Cyber Security in Business / Organizations
- Importance of Cyber Security in the Banking Sector
- Types of Common Cyber Security Attacks
- Volume and Complexity of Cyber Attacks
- How to Protect your Organization Against Cybercrime?
- How Can Individuals Become Better at Protecting Their Data?
- Top Cyber Security Certifications in 2025
- Challenges of Cyber Security
- Conclusion
In the age of internet, our lives are increasingly dependent on online shopping, banking, and socializing. We store photos and personal information on our computers and in the cloud. As more and more aspects of our lives move online, so does the risk of cybercrime. Cybersecurity is the practice of protecting computer systems and networks from unauthorized access or attack.
Individuals, businesses, and governments must invest in cybersecurity to protect their data and assets from criminals. The importance of cyber security in this progressively internet-centered world is supreme. To understand what cyber security is and its importance, you can apply for specialized IT Security certifications online. These courses will upgrade your intuitive skills and allow you to engage with experts in the industry.
What is Cyber Security and Why is it Important?
Cybersecurity is the practice of protecting electronic information by mitigating information risks and vulnerabilities. Information risks can include unauthorized access, use, disclosure, interception, or data destruction.
The importance of cybersecurity in the digital world is immense. It is because the volume and sophistication of cyberattacks are constantly increasing. As our dependence on technology grows, so does our vulnerability to these attacks. Cybersecurity helps to protect our data and systems from these threats.
Why is it Important to Learn about Cybersecurity?
The importance of cybersecurity awareness cannot be taken lightly. Every individual must stay up-to-date and be enlightened with the increasing features of the digitalized world. One reason is that the internet has become an integral part of our lives. We use it for everything from shopping to banking to keeping in touch with friends and family. And as we use it more and more, we are putting more and more of our personal information online. Unfortunately, this information can be used to steal our identity, money, or data.
As we become more reliant on technology, the stakes are getting higher. For example, a cyber-attack could disable a hospital, bring down a power grid, or even start a war. Finally, it is important to learn about cybersecurity because it is a growing industry. There are more and more job opportunities in cybersecurity, and the field will only continue to grow.
Importance of Cyber Security in the Digital World
The importance of cyber security in the digital world cannot be understated. A single security breach can have far-reaching consequences in today's interconnected world. Cybersecurity remains a critical concern in 2024, driven by escalating cyber threats and their profound impact on organizations globally. The average cost of a ransomware attack has surged to $4.54 million, with only 8% of businesses recovering all their data post-payment according to a study by Cobalt. The stats also highlighted that the phishing attacks continue to dominate, comprising 39.6% of all email threats, while 94% of malware is delivered via email.
Emerging technologies like generative AI are exacerbating risks, enabling more sophisticated social engineering attacks. The financial toll of cybercrime is staggering, with damages expected to reach $10.5 trillion by 2025. As businesses increasingly depend on digital infrastructure, integrating strong cybersecurity measures and continuous monitoring is essential to mitigate these evolving threats, emphasizing the importance of cybersecurity in the current world.
Importance of Cyber Security for Students
Cyber security is important for students because they often target cyber attacks. In a recent case, a group of students from a college in the United States was targeted by hackers who gained access to their personal information, including their Social Security numbers and credit card information.
The hackers then used this information to fraudulently charge thousands of dollars to the students' credit cards. The students were left with massive debt and had to spend months repairing their credit. This case highlights the importance of cyber security for students, who are often the victims of cybercrime.
If a student's personal information is stolen in a cyber attack, it could be used to commit identity theft. It could ruin the student's credit, making it difficult for the student to get loans for college or a car. In extreme cases, identity theft can even lead to jail.
Importance of Cyber Security in Business / Organizations
The importance of Cyber Security for businesses and organizations can be seen in the case of the target data breach. In this case, hackers were able to gain access to the target's customer data, including credit and debit card information. It led to target having to pay out millions of dollars in damages and losing customer trust. Target's data breach is just one example of how cyber security is important for businesses and organizations.
Another data breach example would be the WannaCry ransomware attack, which targeted businesses and organizations worldwide. This attack resulted in the loss of data and money for many organizations, and some were even forced to shut down.
Certified Ethical Hacking courses for individuals to work towards protecting data from breaches and malware. You can take this course and understand in detail about cyber security.
Importance of Cyber Security in the Banking Sector
A real-life example of the importance of cyber security for the banking sector is the 2014 JPMorgan Chase data breach. In this breach, hackers gained access to the names, addresses, phone numbers, and email addresses of 76 million households and 7 million small businesses. The hackers also gained access to the account information, including account numbers and balances, of 83 million JPMorgan Chase customers.
This breach highlights the importance of cyber security for the banking sector, as hackers were able to gain access to a large amount of sensitive customer data. If this data had fallen into the wrong hands, it could have been used for identity theft, fraud, or other malicious purposes.
Types of Common Cyber Security Attacks
In recent years, there have been several high-profile cyberattacks that have had a devastating impact on businesses and individuals. These are theft of social security numbers, bank account details, credit card information, and sensitive data leaks. The main reason is that most individuals store their data on cloud storage services such as Dropbox or Google Drive.
These attacks have highlighted the importance of having strong cybersecurity measures in place. Some of the most common cyberattacks include:
1. Phishing Attacks
Master Right Skills & Boost Your Career
Avail your free 1:1 mentorship session
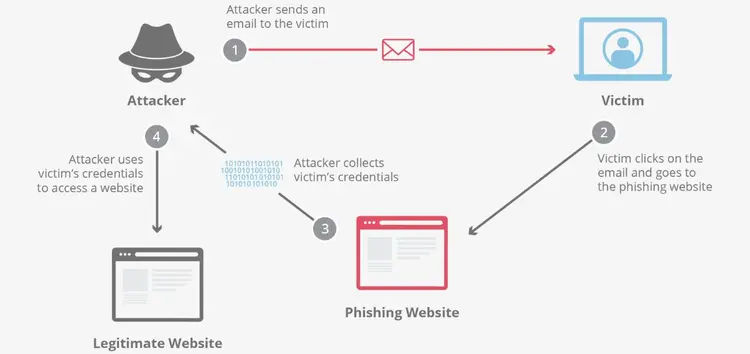
Phishing is a type of cyberattack that involves tricking users into clicking on malicious links or attachments. It can lead to the theft of sensitive information, such as login credentials or financial data.
2. Malware Attacks: Malware is a type of malicious software that can infect computers and devices. It can steal information, hijack devices, or launch attacks on other systems.
3. Denial-of-service Attacks: A denial-of-service attack is a type of attack that prevents users from accessing a system or service. This can be done by flooding the system with traffic or requests or damaging it so it can no longer function properly.
4. Ransomware Attacks: Ransomware is malware that encrypts files or systems and demands a ransom to decrypt them. It can lead to the loss of essential data or the complete shutdown of a system.
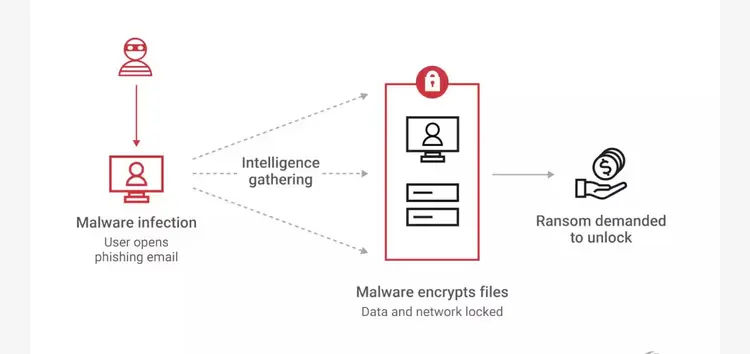
5. Man-in-the-middle (MitM) Attacks: A MitM attack is a type of attack where an attacker intercepts communications between two parties. This can be done by eavesdropping on a network connection or redirecting traffic to a malicious server.
6. SQL Injection: A SQL injection attack is a type of cyber-attack that exploit vulnerabilities in web applications to inject malicious SQL code into the database. This code can view, delete, or modify data in the database. SQL injection attacks can also take control of the server or carry out other malicious activities.
Cybersecurity is critical because it helps to protect us from these and other threats. By being aware of the risks and taking steps to mitigate them, we can help to keep our data and systems safe. Take a look at the need for cybersecurity in the growingly digitalized world.
Volume and Complexity of Cyber Attacks
Cybersecurity is critical in today's digital world as it helps protect organizations and individuals from cyber-attacks. It prevents data breaches, identity theft, and other types of cybercrime, ensuring that organizations safeguard their data and customers.
- Technology Innovation: Cybersecurity protects intellectual property and ideas from theft, allowing companies to maintain a competitive edge and keep their products safe from competitors. This ensures that new products are not easily replicated or stolen before release.
- Cloud Transformation: The cloud has revolutionized IT by introducing agility and responsiveness but also new security risks. Organizations must ensure their cloud providers have adequate security controls and use cloud security platforms to manage and monitor their environments.
- Impact on Business Operations: The rise in internet usage has led to increased cyber-attacks, significantly impacting business operations. Cybersecurity helps protect businesses from data breaches, phishing scams, and ransomware, ensuring data, customer, and reputation protection.
- Maintaining Customer and Employee Trust: Businesses must invest in cybersecurity measures to protect customer and employee data, maintaining trust. Steps like installing firewalls, encrypting data, and creating secure passwords show commitment to information protection.
- Securing Financial Position: Cybersecurity ensures an organization's financial stability by protecting sensitive data and preventing breaches that could damage reputation and bottom line. A cyberattack can lead to customer confidence loss, increased costs, and stock value drops.
- Staying Strong Amidst Competition: Investing in cybersecurity improves a business’s security posture, making it harder for attackers to penetrate systems. This gives companies a competitive edge over those that have not invested in cybersecurity.
- Avoiding Fines and Penalties: Strong cybersecurity measures protect businesses from data breaches and cyber-attacks, helping them avoid potential fines and penalties.
- Preserve the Organization's Ability to Function: Cybersecurity protects against threats that can cause data loss, operational disruption, and financial losses. A robust incident response plan and employee training are crucial aspects of a strong cybersecurity framework, minimizing the impact of cyberattacks.
How to Protect your Organization Against Cybercrime?
To protect your organization against cybercrime, you should take several precautions. First, you should have a solid cyber security policy in place. This policy should include data encryption, firewalls, and intrusion detection systems.
Additionally, you should train your employees to spot and report possible cyber threats. Understanding the Importance of Cyber Security is crucial in maintaining your organization's safety. Finally, you should regularly monitor your network for any suspicious activity. If you take these steps, you will significantly reduce the chances of your organization becoming a victim of cybercrime.
How Can Individuals Become Better at Protecting Their Data?
There are many reasons why individuals need to protect their data. One reason is that if data is not covered, unauthorized people can access and use it. As a result, it can lead to identity theft, fraud, and other crimes.
Another reason is that if data is not protected, it can be lost or destroyed, which can cause significant inconvenience or even financial hardship. Some ways individuals can become better at protecting their data are:
- Use Strong Passwords: Passwords should be at least eight characters long and include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessed words like your name or birthdate.
- Use a Password Manager: A password manager can help you keep track of your passwords and generate strong ones.
- Don't Reuse Passwords: Reusing passwords makes it easier for hackers to access your accounts.
- Keep Your Software up to Date: Software updates often include security patches that can help protect your data.
- Use Two-factor Authentication: Two-factor authentication adds an extra layer of security by requiring you to enter a code from your phone or email in addition to your password.
- Be Cautious of Phishing Scams: Phishing scams are emails or websites that pose as a legitimate company to trick you into entering your personal information.
- Back up Your Data: Backing up your data helps ensure you can still access it even if your computer is lost or stolen.
Top Cyber Security Certifications in 2025
The demand for skilled cybersecurity professionals continues to grow, making certifications a valuable asset for career advancement. Here are some of the top certifications that can help you enhance your expertise and credibility in the cybersecurity field.
- Certified Information Systems Security Professional (CISSP): Offered by (ISC)², CISSP is a globally recognized certification that validates an individual's expertise in cybersecurity. This certification is ideal for experienced security practitioners, managers, and executives.
- Certified Ethical Hacker (CEH): Provided by the EC-Council, the CEH certification is designed for professionals who want to understand and counteract hacking tactics. CEH is highly respected in the cybersecurity community and is ideal for penetration testers and security consultants.
- KnowledgeHut Cybersecurity Bootcamp: This certification from KnowledgeHut focuses on equipping professionals with practical skills in cybersecurity.
- Certified Information Security Manager (CISM): Offered by ISACA, the CISM certification is aimed at management-focused individuals who design and manage an enterprise's information security program. CISM is recognized globally and is ideal for IT managers and security professionals looking to move into a leadership role.
Challenges of Cyber Security
- Increasing Levels of Cyber Attacks: Cyber attackers are leveraging advanced technologies, including AI and machine learning, to create more sophisticated and harder-to-detect threats. This includes more realistic phishing attempts and automated hacking tools.
- Rising Costs of Cybercrime: Cyber attacks are becoming increasingly costly for organizations, not just in terms of immediate financial loss but also considering long-term impacts such as reputational damage, loss of customer trust, and increased expenses for recovery and prevention measures.
- Increasing Use of IoT Devices: The widespread use of IoT devices has expanded the attack surface, making networks more vulnerable. Weak security protocols in these devices provide easy entry points for cyber attackers.
- Remote Work Vulnerabilities: The shift to remote work has introduced new security challenges, including unsecured home networks and personal devices accessing corporate resources, increasing the risk of cyber attacks.
- Data Privacy Regulations: Compliance with evolving data privacy laws, such as GDPR and new regulations like Quebec’s Law 25, adds complexity to cybersecurity management. Organizations must continuously update their policies to remain compliant.
- Shortage of Cybersecurity Professionals: The demand for skilled cybersecurity professionals far exceeds supply, leading to a talent gap that makes it difficult for organizations to protect their systems effectively.
- Evolving Ransomware Tactics: Ransomware attacks are becoming more frequent and complex, with cybercriminals employing extortion tactics and backdoors to maximize their impact.
- Supply Chain Attacks: Cyber attackers are increasingly targeting supply chains to exploit vulnerabilities in third-party vendors, which can have cascading effects on the primary organization.
- Nation-State Cyber Threats: Nation-state actors continue to pose significant threats, particularly targeting critical infrastructure and significant events like elections and the Olympics, potentially causing widespread disruption.
- Generative AI Risks: Generative AI tools can be used to create malicious code and sophisticated phishing emails, posing new security challenges that require innovative defenses and continuous monitoring.
Unlock the power of ITIL with our comprehensive ITIL training program. Gain the skills and knowledge to streamline your IT processes and drive business success. Enroll now!
Conclusion
As the world becomes increasingly digitized, the need for strong cybersecurity measures becomes more and more apparent. Businesses of all sizes need to be aware of the potential risks and take steps to protect themselves and their customers. In addition, students can also pursue KnowledgeHut Security certifications to grasp the concept of cybersecurity.
The importance of cyber security is that organizations that need cybersecurity always deploy measures to ensure solid and safe data retention. Moreover, individuals also need to be vigilant about their online activity and take steps to protect their personal information. We can help make the internet safer for everyone with the right precautions.
Frequently Asked Questions (FAQs)
1. What are the five benefits of using cyber security?
2. What is the most crucial thing in cyber security?
3. What are cyber security and its advantages?
4. Why is cyber security important to business?
5. What are the benefits of data security?
Get Free Consultation
By submitting, I accept the T&C and
Privacy Policy
